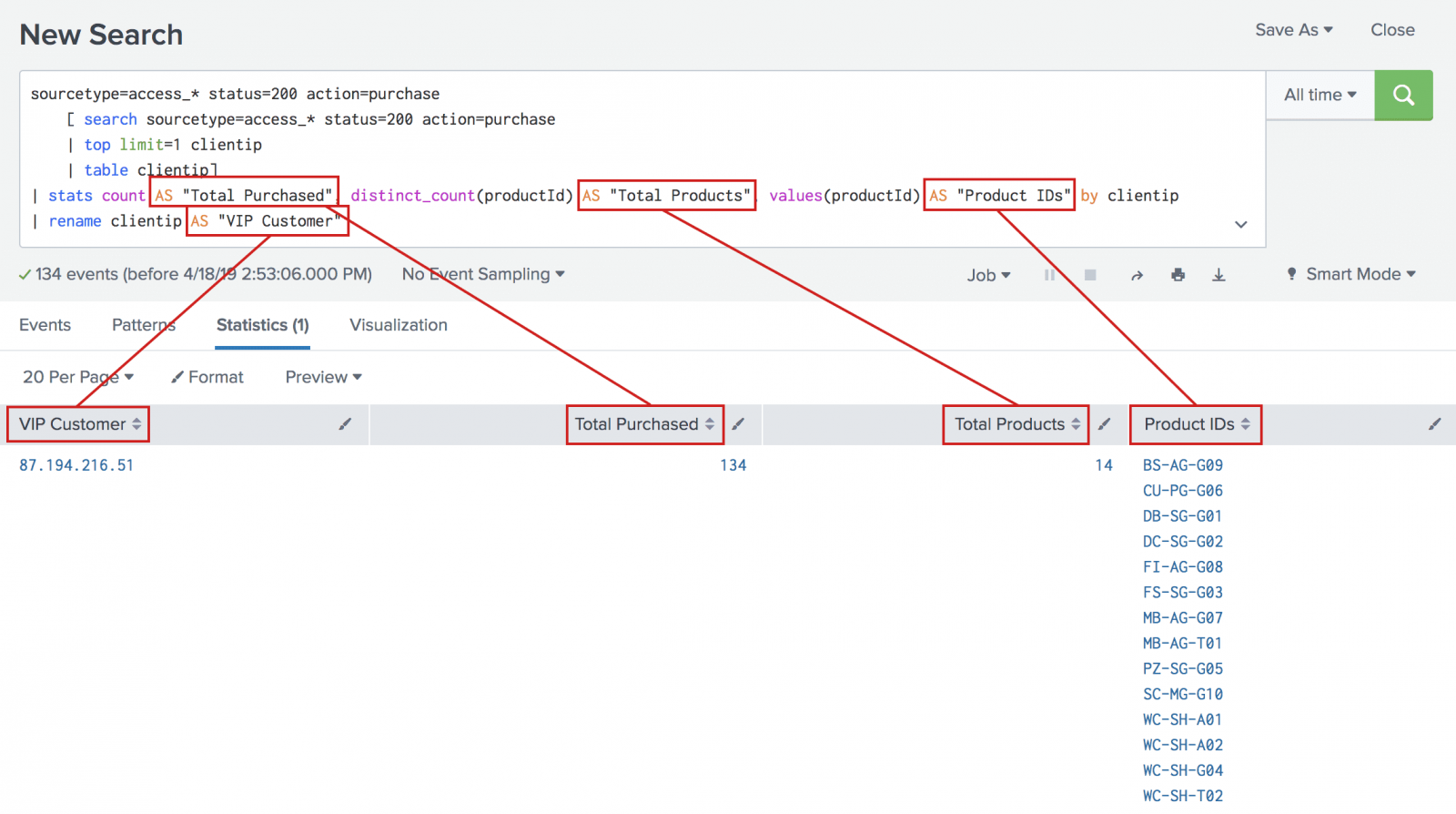
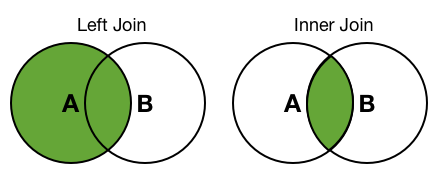
Splunk is a powerful software platform that enables organizations to search, analyze, and visualize large amounts of machine-generated data in real-time. One of the key features of Splunk is its ability to perform complex searches and data analysis using a variety of techniques, including subsearches and joins. Subsearches and joins are two techniques that allow users to combine data from multiple searches or data sources in Splunk. These techniques are particularly useful when dealing with large and complex datasets that require advanced analysis and correlation. A subsearch is a technique that allows users to use the results of one search as input to another search. This can be extremely useful when you want to narrow down your search results based on specific criteria or conditions. For example, you may want to find all the events in your log data that occurred at the same time as a specific error message. By using a subsearch, you can first search for the error message and then use the results of that search to find all the events that occurred at the same time. To perform a subsearch in Splunk, you can use the "| search" command followed by the subsearch query enclosed in square brackets. For example, if you want to find all the events that occurred at the same time as a specific error message, you can use the following search query: ``` index=your_index | search [search index=your_index error_message="specific_error_message" | fields _time] ``` In this example, the subsearch query `search index=your_index error_message="specific_error_message" | fields _time` is enclosed in square brackets and is used to filter the events based on the specified error message. The subsearch query returns the _time field from the events that match the specified error message, which is then used as input for the outer search query. Joins, on the other hand, are used to combine data from multiple data sources or searches based on common fields or criteria. This technique is particularly useful when you want to correlate data from different sources or perform advanced analysis that requires data from multiple sources. For example, you may want to combine log data with data from a database or external system to perform more comprehensive analysis. To perform a join in Splunk, you can use the "| join" command followed by the fields to join on and the data source or search to join with. For example, if you want to join log data with data from a database based on a common field, you can use the following search query: ``` index=your_index | join common_field [search index=your_database | fields common_field, additional_field] ``` In this example, the join command is used to join log data from index=your_index with data from a database based on the common_field. The subsearch query `search index=your_database | fields common_field, additional_field` is used to retrieve the common_field and additional_field from the database. The join command then combines the log data with the database data based on the common_field. When using subsearches and joins in Splunk, it is important to optimize your searches to ensure efficient and accurate results. Here are some tips to help you optimize your searches: 1. Use field extractions: Field extractions allow you to extract specific fields from your data, which can improve search performance and reduce resource usage. Make sure to define field extractions for common fields that you will be using in subsearches and joins. 2. Narrow down your searches: Use filters and specific search criteria to narrow down your searches and reduce the amount of data that needs to be processed. This can significantly improve search performance, especially when dealing with large datasets. 3. Use summary indexing: Summary indexing allows you to pre-calculate and store summary data, which can be used in subsearches and joins. This can improve search performance by reducing the amount of data that needs to be processed in real-time. 4. Optimize subsearches: When using subsearches, make sure to limit the number of events returned by the subsearch query. Use the `| fields` command to only retrieve the fields that you need for the outer search query. 5. Consider data model acceleration: Data model acceleration is a feature in Splunk that allows you to pre-calculate and store summary data for specific data models. This can significantly improve search performance when working with complex data models and large datasets. By following these optimization tips and using subsearches and joins effectively, you can unlock the full potential of Splunk and perform advanced analysis and correlation on your machine-generated data. Whether you are looking to narrow down your search results, combine data from multiple sources, or perform complex analysis, subsearches and joins in Splunk can help you achieve your goals efficiently and accurately.
join - Splunk Documentation

women looking to fuck in clarksville
. A subsearch is a search that is used to narrow down the set of events that you search on. The result of the subsearch is then used as an argument to the primary, or outer, search.. How to combine my two search queries using join or subsearch?. Splunk Answers Using Splunk Splunk Search How to combine my two search queries using join or. How to combine my two search queries using join or subsearch? allladin101 Explorer 11-03-2014 10:07 AM Hi, I have 2 queries which do not have anything in common, how ever i wish to join them can somebody help : query 1 :. sub-search and then join with another search - Splunk Community. 05-24-2018 05:08 AM Hi, had facing issues in using join command , i have two search (sub-search, search)which needs to be joined together splunk join subsearch. sub search : "C:WindowsSystem32windows.exe" sourcetype=windows [search sourcetype=scanner | dedup FQDN | rename FQDN as ComputerName] |table Process ComputerName search sourcetype=scanner | dedup FQDNfuck local asains today
sierra trading post u00b7 holiday sweepstakes
. Joining two queries not giving the desired result. I have 2 queries and joining it with "Join" using the common field "SessionID". With the below query Im just getting the results if there are results from both the searchoxford street sydney gay bars
. If there is no result for either the parent search or the sub search the result is not getting printed.. How to Use the Splunk Join Command - Kinney Group. What is the Join Command in Splunk? The join command brings together two matching fields from two different indexes splunk join subsearch. To use the join command, the field name must be the same in both searches and it must correlate to two data sets.. Using and Understanding Basic Subsearches in Splunk. A subsearch in Splunk is a unique way to stitch together results from your data. Simply put, a subsearch is a way to use the result of one search as the input to another splunk join subsearch. Subsearches contain an inner search, whos results are then used as input to filter the results of an outer search.. Combining multiple data sources in SPL - Splunk Lantern. The most intuitive command to use when these situations arise is the "join" command, but it tends to consume a lot of resources - especially when joining large datasets. splunk join subsearch. the Splunk platform processes the subsearch first as a distinct search job and then runs the primary search. Pros splunk join subsearch. Merges data from multiple data sources; Runs searches .. How to do a subsearch in Splunk? - DEV Community. So when you are doing this kind of search as a subsearch, Splunk transforms it to OR condition for each line splunk join subsearch. [search error_code=* | table transaction_id ] AND exception=* becomes (transaction_id = "1" OR transaction_id = "2" OR transaction_id = "3") AND exception=*. Re: How to exclude users from service account valu . - Splunk Community. Debug the query by running the commands before the first | in a new query. Verify the desired fields are present. Add the commands up to the next | and verify the fields are still there. Repeat the process until the fields disappear and youll have found the source. Post the details if you need help determining the cause.dosi pop strain leafly
. Usage Of Splunk Commands : Join - Splunk on Big Data. Usage Of Splunk Commands : Join Hi everyone !! Today we will learn about Join command. It is a very important command of Splunk, which is basically used for combining the result of sub search with the main search and importantly one or more fields should be common in both the result-sets. Syntax:sex surrogate ottawa
. SUBSEARCH - Splunk on Big Data. 4112 0 Spread our blog SUBSEARCH Definition: 1) A subsearch is a search that is used to reduce the set of events from your result set splunk join subsearch. 2) The result of the subsearch is used as an argument to the primary or outer search. 3) Subsearches must be enclosed in square brackets and must start with a Generating command (eg: search, makeresults etc.).. Splunk! How To Splunk JOIN Subsearch Outer Search Example. How To Splunk JOIN Subsearch Outer Search Example - YouTube Splunk! How To Splunk JOIN Subsearch Outer Search Example moviestudioland 6.53K subscribers Subscribe 4.7K views 3 years ago Data.